BizTalk applications are associated with heaps of files used for receiving and transmitting messages. To ensure smooth business processes, it's crucial to monitor file availability and regular transmissions. To minimize the risk of disruptions and reduce manual intervention, BizTalk360 offers essential metrics monitoring, covering file availability, count, directory size changes, and file age. With this user can configure thresholds for critical parameters and automate the tracking process of file locations.
This section explains how you can monitor your File Locations. Check the below articles to learn how to set up monitoring:
- File - Monitor the number of files in File shares.
- FTP - Monitor the number of files in FTP sites.
- SFTP - Monitor the number of files in SFTP sites.
- Mailbox - Monitor the availability of POP3 and Office365 Mailbox
Integrate Automated Tasks
By integrating Automated Tasks into File, FTP, or SFTP mappings, the system will automatically trigger the actions such as starting or stopping the artifacts, Applications, Host Instances , NT Services etc.
For instance, you can set up a threshold rule to monitor the file count and initiate an automated action if the count exceeds the threshold limit. Also define the threshold level at when the action should occur, such as during an error or warning violation.
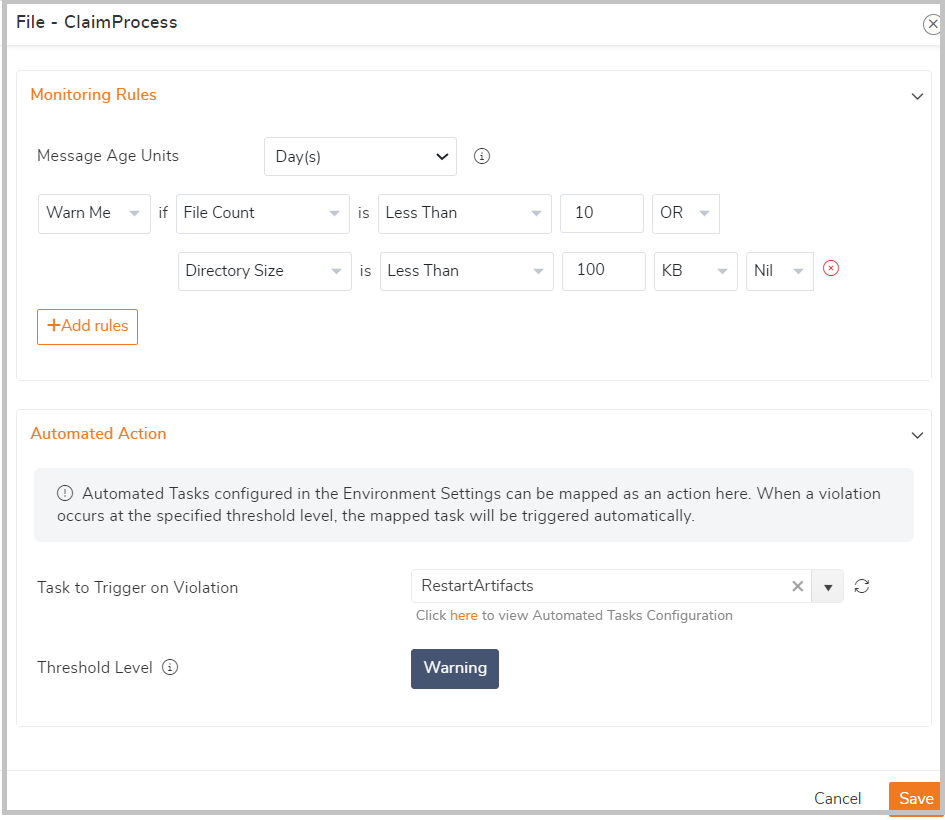
Automate Host Instance Restart
You have the option to enable automatic restart of the host instance in the event of a threshold violation caused by files getting stuck in the receive location.
The configuration for restarting the host instance can be set up in the environment settings, as explained in detail in this documentation.
After completing the configuration, enable it for the necessary file location (receive location) threshold monitoring configuration.
Here's an example scenario illustrating how automated restart of host instances on detecting violations is helpful.
Consider an organization that occasionally experiences network outages due to external factors. As a result, files are not being processed by the BizTalk FILE/(S)FTP receive locations, even though the respective ports are in enabled state. Upon detailed investigating, it is found that restarting the host instance associated to the ports resolves the issue and allows the files to be processed.
In such case, instead of manually dealing with this situation every time, you can set up a monitoring rule as mentioned in the below image. This rule triggers an error alert if there are more than 10 files present in the folder for longer than 30 minutes, indicating that the files are not processed for a long time.
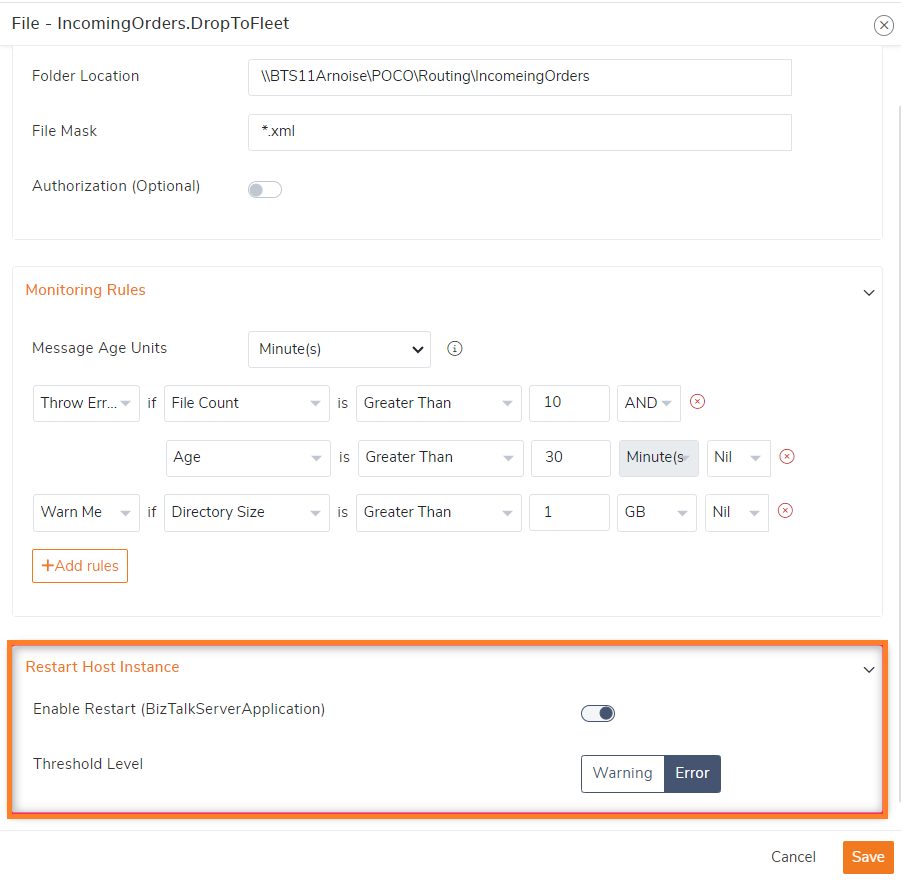
By enabling the automatic restart of the host instance on Error condition will attempt to restart the associated Host Instance, thus effectively solving the problem without any manual intervention. This eliminates the time-consuming process of determining where the error occurred, and which host instance needs to be restarted.