The Automated Task feature in BizTalk360 allows for automatic handling of certain administrative tasks such as starting or stopping the artifacts, NT Services, App Pools and Logic Apps, or executing PowerShell scripts. When the Automated Tasks integeration with Alarms becomes a powerful integration, for maintaining the health and performance of the BizTalk environment by automatically taking action incase if any threshold violation .
Use Case: Healthcare Claims Processing
A healthcare organization uses BizTalk Server to process insurance claims. The system includes multiple orchestrations, send ports, and receive locations. The claim is expected to process within 10 mins.
The challenge here is the system may susceptible to failures due to any reason. These failures can lead to delays in claim processing. This can be solved by monitoring the file location , enabling automated action to restart the Application or HostInstance.
Solution:
- Configure Alarms: Create an alarm to monitor a file location where incoming claims are dropped. Configure threshold rule to trigger if files are not processed within 10 minutes.
- Define Automated Tasks: Create automated tasks to move unprocessed files by starting specific Application , Artifacts or Host Instances.
- Enable Automated Action in Alarm Mapping: Map the created task in the file monitoring configuration. When the alarm detects unprocessed files, the task automatically gets triggered which helps to moves the files , ensuring the system can reattempt processing the claims.
Integrate Automated Task with Alarm Mapping
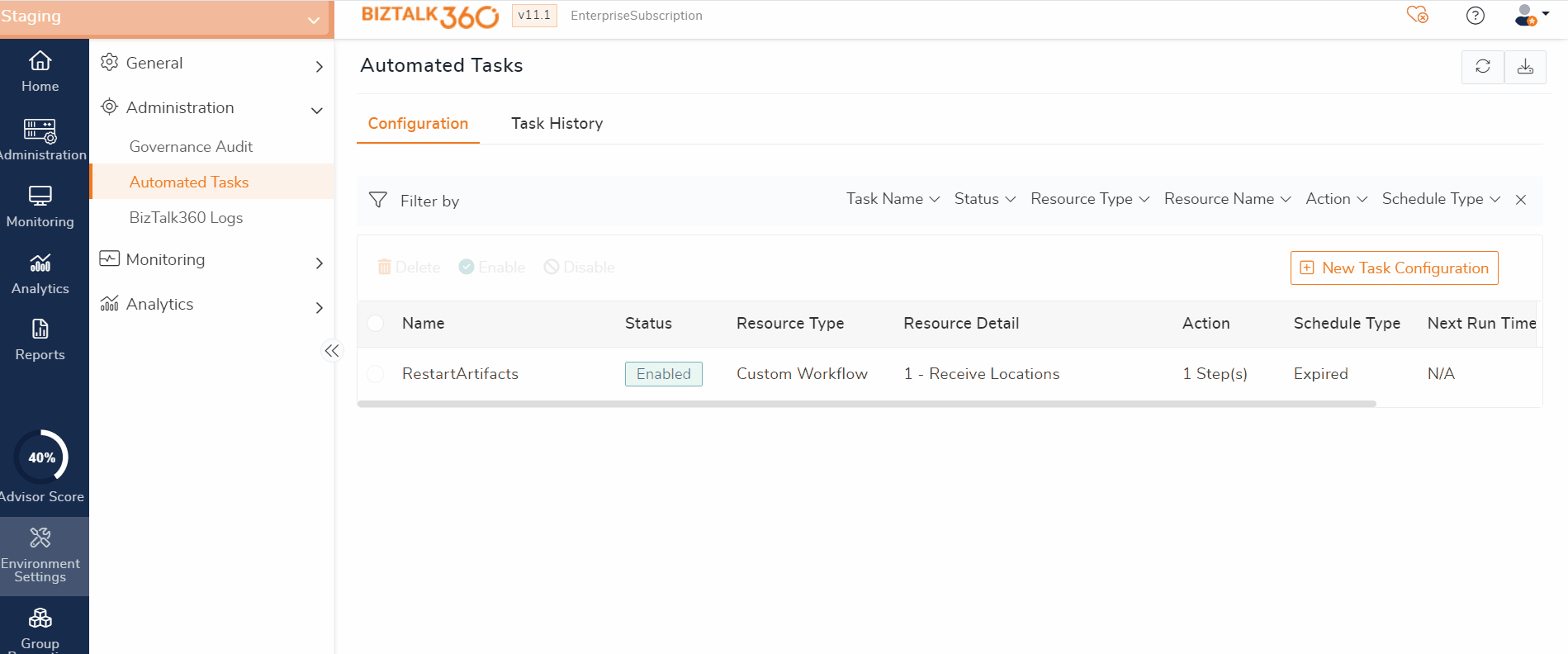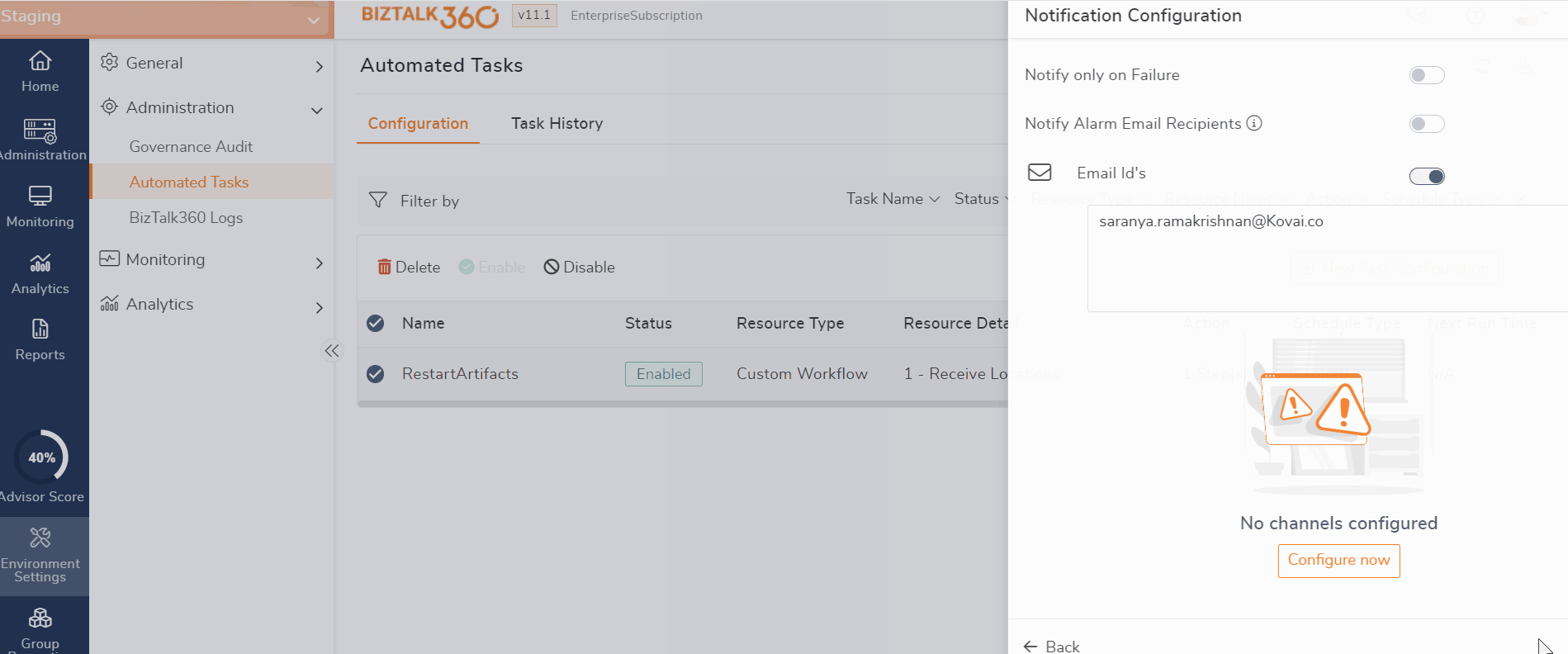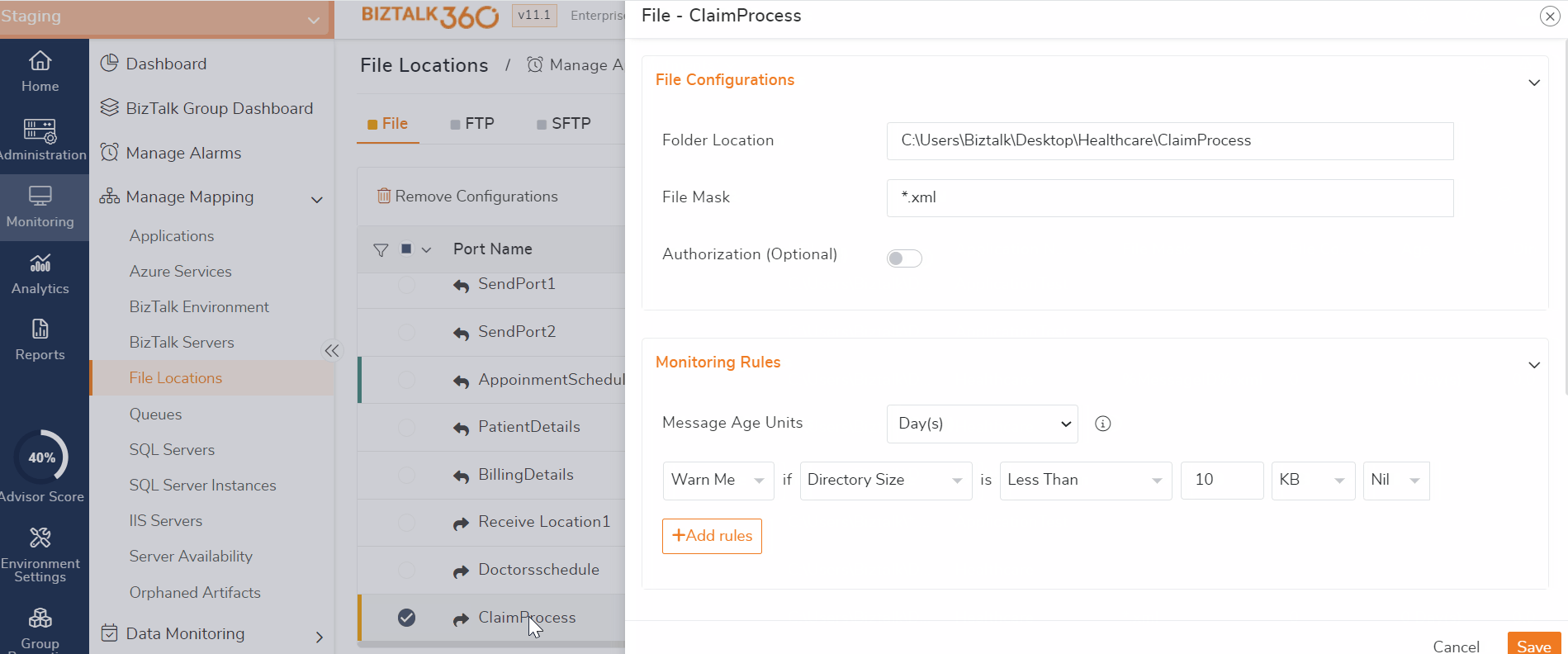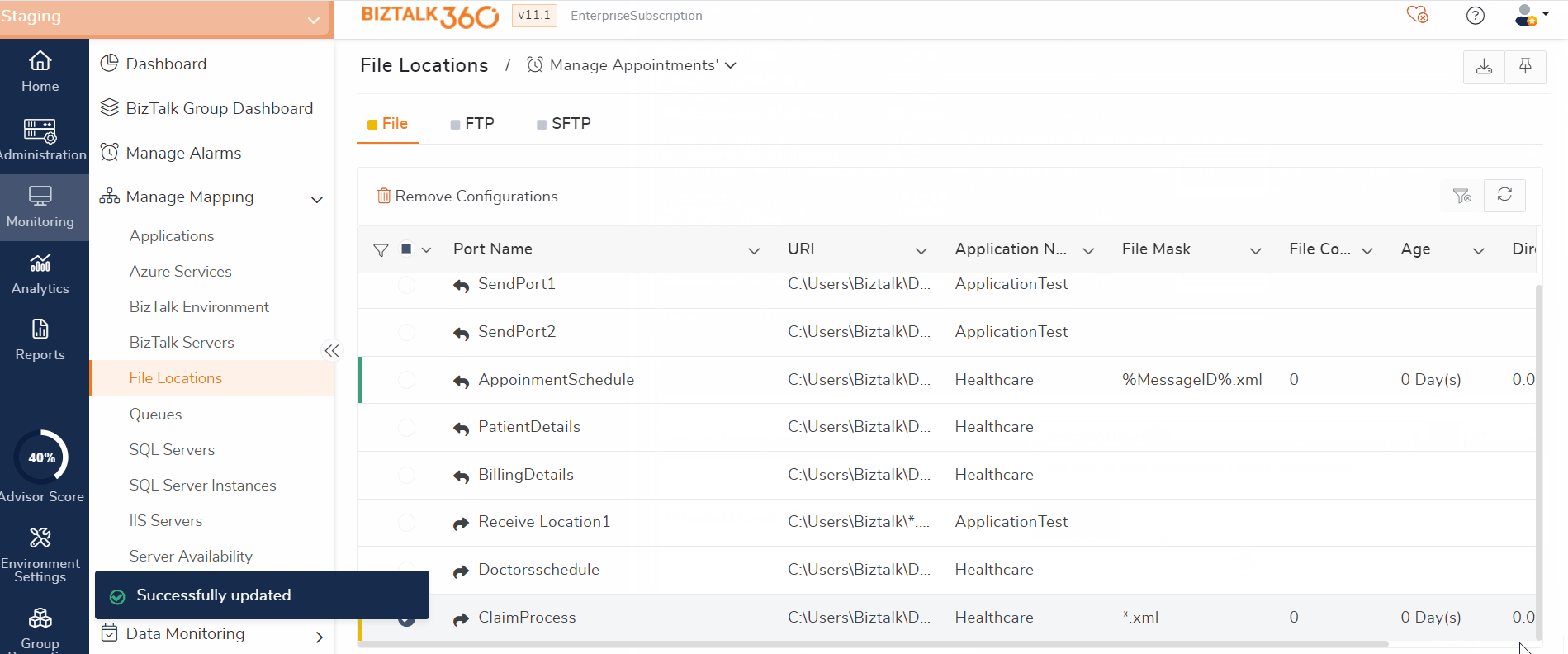
1) Create Automated Task
- Navigate to Environment Settings->Automated Task ->New Task Configuration
- In The New Task Configuration select the Task type(Custom,BizTalk Application,Artifacts,Host Instance,NT Services,IIS App Pool,Powershell script) which will open the task configuration blade . Update the configuration based on the business need.
Read the document to understand more about Automated Task and how to configure different types of Tasks.
2) Configure Rule Monitoring
- Create Alarm for any threshold rule monitoring .
- Choose the rule monitoring configuration, such as File Locations, Queues, Web Endpoints, Service Instances .Configure specific threshold rules, for example, Directory Size greater than 10 or Active Messages in Queue more than 3 ,based on your business need.
- Application Monitoring -> Service Instances
- BizTalk Environments Monitoring -> Host Throttling, DB Query, DB size
- BizTalk servers Monitoring -> Disk , System resources, Event logs
- SQL Servers Monitoring -> Disk , System resources, Event logs
- File Locations Monitoring -> Files, FTP, SFTP
- Queues Monitoring -> MSMQ, IBM MQ, Rabbit MQ.
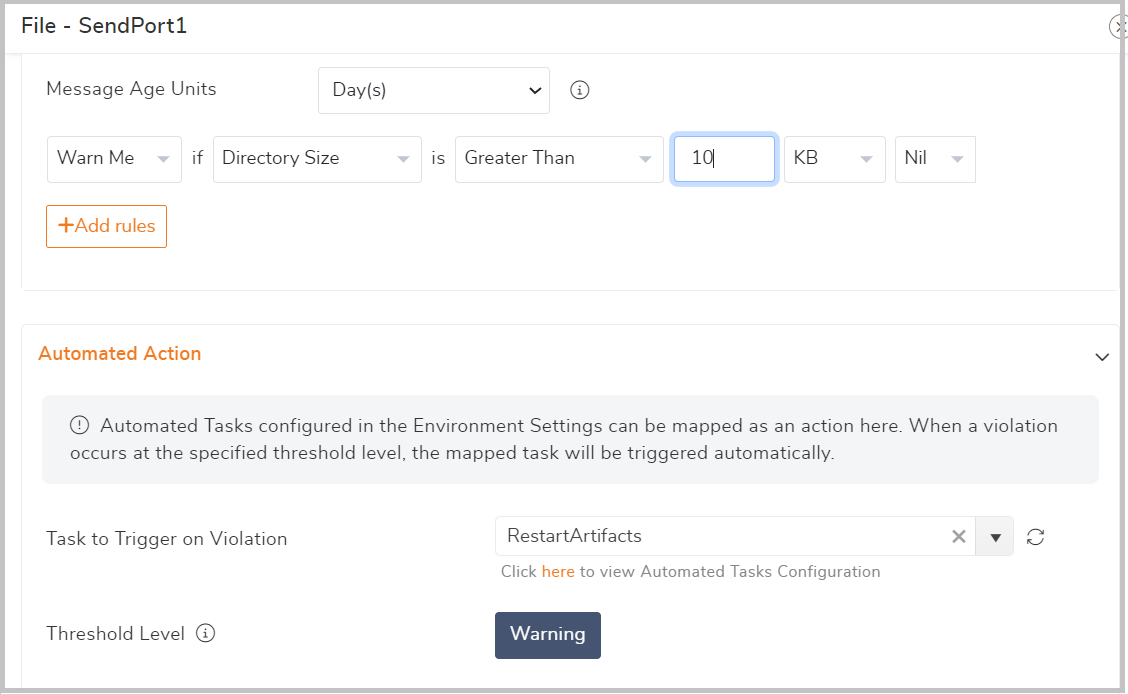
- Configure Automated Action: Select the Automated Task you want to trigger when the threshold rule is violated. Then, choose the Threshold Level at which the task should be triggered, i.e during a warning or error violation.
For example, if you want to monitor a file location and ensure that the directory size is less than 10 KB, you can set up an Automated Task to restart the receive location automatically if this condition is met. This task will be executed whenever the monitoring detects that the directory size exceeds the expected threshold.
Auditing and Notification
Whenever a task is executed, it will be audited in both the governance audit section and the Task history, including details such as the time period and a summary of the violations detected.
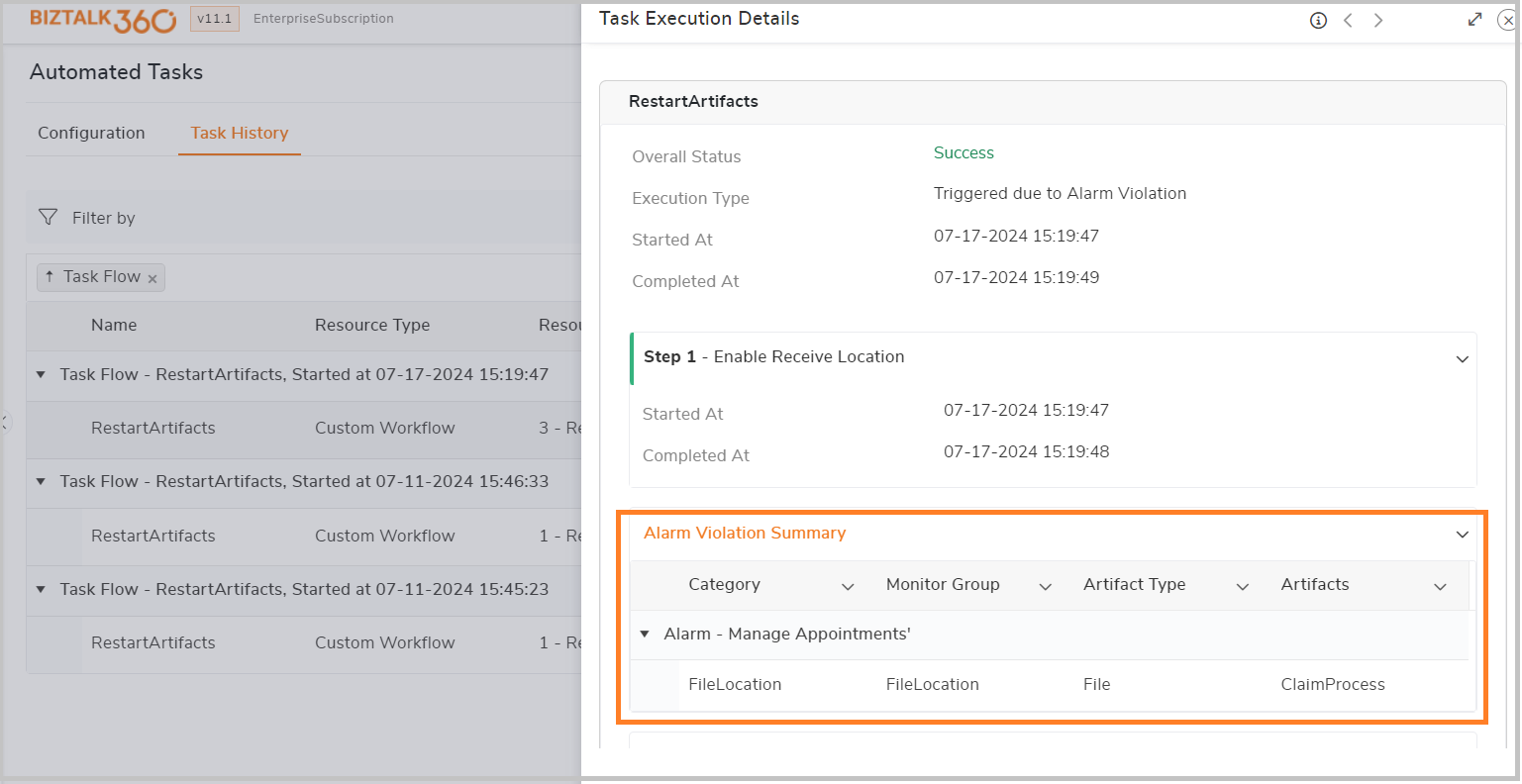
When a task is executed due to a threshold rule violation, an alert will be sent to the configured email ID, including a summary of the violation that caused the task to trigger automatically.
Points to Remember
- This integration is applicable only for rule-based monitoring, such as monitoring file locations, queues, web endpoints, system resources, service instances ,event log monitoring etc . It is not designed for state-based monitoring. For state-based monitoring, you can use the Auto Correct functionality to take automatic actions.
- Once a task is mapped with an alarm, it will continue to execute whenever a violation occurs in the mapped artifacts, regardless of the task schedule creation. which means even if the task was created for one-time execution or if the task schedule has expired, the task will still be triggered by any violations.
- Single Execution for Multiple Mappings: When the same task is mapped to multiple alarms, it will only execute once if violations occur in both mappings.
- Re-Execution: If a violation clears in one mapping but persists in another, there will be a 15-minute delay before the task is executed again.